[ad_1]

Threat actors have been distributing destructive apps below the guise of seemingly harmless purchasing applications to concentrate on clients of 8 Malaysian banking companies due to the fact at least November 2021.
The attacks included placing up fraudulent but authentic-searching sites to trick users into downloading the applications, Slovak cybersecurity firm ESET said in a report shared with The Hacker Information.
The copycat websites impersonated cleansing products and services these types of as Maid4u, Grabmaid, Maria’s Cleansing, Maid4u, YourMaid, Maideasy and MaidACall and a pet keep named PetsMore, all of which are aimed at consumers in Malaysia.
“The risk actors use these faux e-shop purposes to phish for banking credentials,” ESET stated. “The applications also ahead all SMS messages received by the target to the malware operators in case they consist of 2FA codes despatched by the financial institution.”
The qualified banking institutions involve Maybank, Affin Bank, Community Bank Berhad, CIMB bank, BSN, RHB, Financial institution Islam Malaysia, and Hong Leong Financial institution.
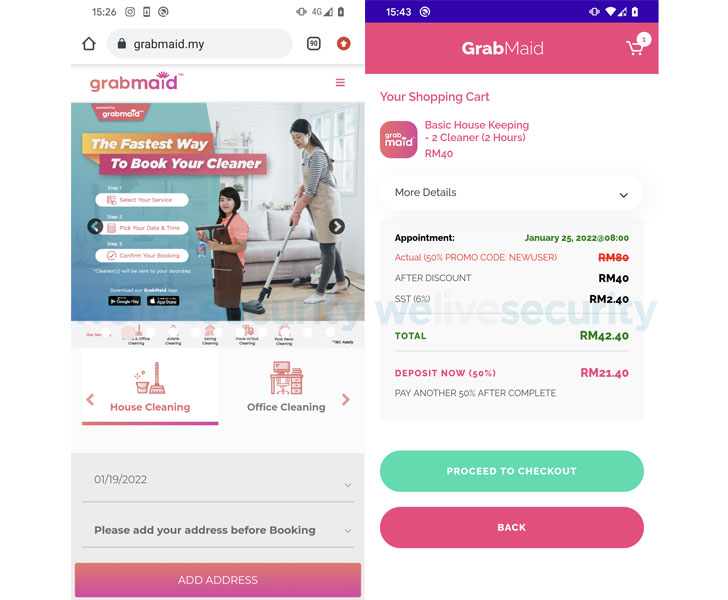
The sites, distributed by Facebook advertisements, urge site visitors to download what the attackers assert to be are Android apps accessible on the Google Perform Store, but in actuality, redirect them to rogue servers under their management.
It can be worth noting in this article that the assault hinges on the prerequisite that the probable victims permit the non-default “Install unknown apps” choice on their gadgets for it to succeed. What is a lot more, 5 of the abused services don’t even have an app on Google Enjoy.
When introduced, the apps prompt the users to signal in to their accounts, allowing them to area bogus orders, adhering to which alternatives are offered to complete the checkout system by including a fund transfer from their lender accounts.
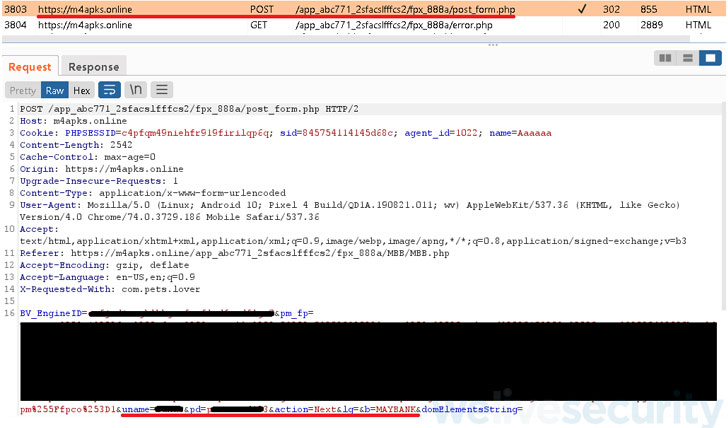
“Right after selecting the immediate transfer option, victims are introduced [with] a fake FPX payment web page and requested to choose their lender out of the eight Malaysian banking institutions provided, and then enter their credentials,” ESET malware researcher Lukáš Štefanko reported.
The top aim of the marketing campaign is to steal the banking credentials entered by the buyers and exfiltrate it to the attacker-controlled server, though displaying an error concept that the entered consumer ID or password is invalid.
In addition, the bogus apps are engineered to accessibility and transmit all SMS messages gained by the consumers to the remote server in the function the lender accounts are secured by two-factor authentication.
“While the campaign targets Malaysia exclusively for now, it may possibly broaden to other international locations and banking companies later on,” Štefanko stated. “At this time, the attackers are after banking qualifications, but they could also empower the theft of credit card facts in the foreseeable future.”
[ad_2]
Source website link


